Gone Phishing: Five Signs That Identify Scam Email Messages
Don’t Freak Out If You Get Blackmail Spam Containing an Old Password
Have you gotten an email message whose Subject line says something like “Change your password immediately! Your account has been hacked.”? If not, it may be only a matter of time before you do. It’s a scary message, especially because it contains one of your passwords, some threats, and a demand for money. Worse, the password is likely one you’ve used in the past—how could the hacker have discovered it? Has your Mac really been taken over?
Relax. There’s nothing to worry about.
This “blackmail spam” has been making the rounds on the Internet recently—we’ve heard from several clients who have received it, and we’ve gotten copies too. The message purports to be from a hacker who has taken over your Mac and installed spyware that has recorded you visiting Web sites that aren’t exactly G-rated. The hacker also claims to have used your Mac’s camera to photograph you while you’re browsing said non-G-rated sites and threatens to share those pictures with your contacts and erase your drive unless you pay a ransom using Bitcoin.
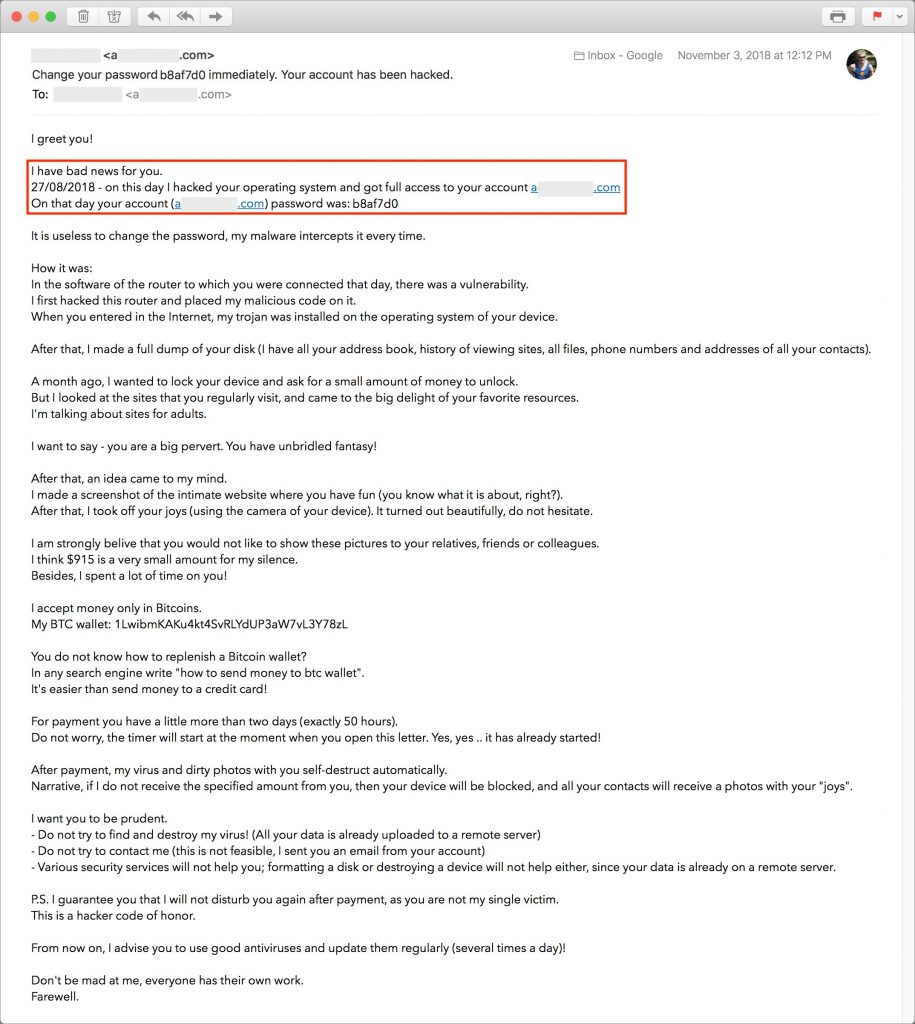
This blackmail spam has raised so many pulses because it backs up its claims by showing a password that you’ve used in the past. Hopefully, it’s not one that you’re still using, because it was extracted from one of the hundreds of password breaches that have occurred over the past decade. Impacted Web sites include big names such as Yahoo, LinkedIn, Adobe, Dropbox, Disqus, and Tumblr—thieves have collectively stolen over 5.5 billion accounts. It’s all too likely that some old password of yours was caught up in one of those thefts.
Concerning as the message sounds, all the details other than your email address and password are completely fabricated. Your Mac has not been hacked. There is no malware spying on your every move. No pictures of you have been uploaded to a remote server. Your hard drive will not be erased. In short, you have nothing to worry about, and you should just mark the message as spam.
However, if you’re still using the password that appeared in the message, that is cause for concern. It means that any automated hacking software could break into the associated account, and it must be a weak password if the bad guys were able to decrypt it from the stolen password files. Go to Have I Been Pwned and search for your email address. If it shows up for any breaches, make sure you’ve changed your password for those accounts.
As always, we recommend that you create a strong, unique password for each of your Web accounts. The easiest way to do this is to rely on a password manager like 1Password or LastPass to generate a random password. Then, when you want to go back to that site, the password manager can log you in automatically. It’s easier and more secure.
If you’re still concerned about your passwords, call us and we can help you get started with stronger security practices.
Watch Out for Phishing Attacks Hidden in Your Email
One of the most important things you can do to stay safe on the Internet is to be careful while reading email. That’s because online criminals know that we’re all busy, and we often don’t pay enough attention to what we’re reading or where we’re clicking.
To take advantage of our inattention, these Internet information thieves forge email messages to look like they come from the likes of Apple, Facebook, and Amazon, along with well-known banks, payment services, retailers, and even government agencies. Even more dangerous are messages that appear to come from a trusted individual and include personal details—these messages are often targeted at executives and company managers. Generally speaking, these attacks are called phishing—you can see examples here.
The goal? Get you to click a link in the message and visit a malicious Web site. That site usually continues to masquerade as being run by a company or organization you trust. Its aim is to sucker you into revealing confidential information by asking you to log in, pay for a product or service, or fill out a survey. The site—or an attachment in the email message—might also try to install malware. Although macOS is quite secure, if you approve security prompts, it can still be infected.
Although phishing is a huge problem that costs businesses hundreds of millions of dollars every year, you can easily identify phishing messages by looking for telltale signs:
- Be suspicious of email messages, particularly from people you don’t know or from well-known companies, that ask you to click a link and do something with an online account.
- Look closely at email addresses and URLs (hover the pointer over a link to see the underlying URL). Phishing messages don’t use official domains, so instead of paypal.com, the addresses and links might use paypa1.com—close enough to pass a quick glance, but clearly a fake.
- Watch out for highly emotional or urgent requests. They’re designed to make you act without thinking. Take any such messages with a grain of salt.
- Channel your inner English teacher and look for poor grammar or odd phrasing, which are red flags for phishing messages. Email from real companies may not be perfect, but it won’t have multiple egregious errors.
So what do you do if you get a message that may be phishing for sensitive information? Most of the time you can just ignore it. If you’re worried that it might be legit, instead of clicking any links in the message, navigate to the site in question manually by typing the organization’s URL into your browser—use a URL that you know to be correct, not the one in the email message. Whatever you do, do not open attachments that you aren’t expecting and never send confidential information via email.
If you think you’ve fallen prey to a phishing attack and given away a password, you’ll want to change passwords on any affected accounts. If you’ve opened any attachments or approved any installs, run anti-malware software to determine whether your Mac has been infected. Contact us if you need help. And remember, regular backups protect you from a multitude of sins.
Twitter: Can you tell if you’ve been targeted by a phishing attack? Read on to learn how to identify malicious messages!
Facebook: Phishing attacks—email containing links that try to get you to reveal usernames, passwords, or credit card details—are all too common these days. Follow our advice to learn how to identify malicious messages.
4 Emails You Should Never Open
Cybercrime is an ever-present threat to modern businesses.
Without up-to-date and varied IT security measures, successful hacks can compromise your customers’ and employees’ sensitive data and harm your systems, resulting in costly downtime, and worse.

Email is the primary tool that companies like yours use for daily communications in the modern business world. It’s simple, it’s easy, and it’s effective, but it’s also the main source of malware and spam that could threaten your business. If you’re not careful, your email could be the key for cybercriminals that are trying to exploit you:
- Viruses and malware disguised as regular attachments from familiar sources.
- Phishing schemes from cybercriminals posing as familiar companies and contacts in an attempt to convince employees to give up sensitive information.
- Spam and junk email clogging up your inbox and blocking real, important emails from your clients and partners.
So what can you do? One of the surest ways to protect your business from a range of threats is to learn about them!
Need To Speak With An Email Security Expert Right Away?
Call In Your Local Email Security Experts at {company} For A No Cost Consultation Of Your Email Systems.
Call {phone}.
No matter how “bomb-proof” we make your network, you and your employees can still invite a hacker in if you click on a link or open an attachment in an email sent by a cybercriminal. Some spam is obvious, but others are very cleverly designed to sneak past all the filters and trick the recipient into opening the door.
Known as a “phishing” email, this still is the #1 way hackers circumvent firewalls, filters and antivirus, so it’s critical that you and your employees know how to spot a threatening email.
Here are four types of email ploys you should be on high alert for:
The Authority Email
The most common phishing emails are ones impersonating your bank, the IRS or some authority figure. The rule of thumb is this: any email that comes in where 1) you don’t personally know the sender, including emails from the IRS, Microsoft or your “bank,” and 2) asks you to “verify” your account should be deleted. Remember, ANY important notification will be sent via old-fashioned snail mail. If it’s important, they can call you.
The “Account Verification” Email
Any email that asks you to verify your password, bank information or login credentials, or to update your account information, should be ignored. No legitimate vendor sends emails asking for this; they will simply ask you upon logging in to update or verify your information if that’s necessary.
The Typo Email
Another big warning sign is typos. Emails coming from overseas (which is where most of these attacks come from) are written by people who do not speak or write English well. Therefore, if there are obvious typos or grammar mistakes, delete it.
The Zip File, PDF Or Invoice Attachment
Unless you specifically know the sender of an email, never, ever open an attachment. That includes PDFs, zip files, music and video files and anything referencing an unpaid invoice or accounting file (many hackers use this to get people in accounting departments to open emails). Of course, any file can carry a virus, so better to delete it than be sorry.
The good news is that there are many steps a small business owner like yourself can take to secure their business’ IT. Some of the most effective ways to combat security breaches are simple tasks that you can perform without having to hire a security expert.
Keep the following in mind:
- Keep Link Clicking to a Minimum: Clicking on links that appear in random emails just isn’t safe. Hyperlinks are commonly used to lead unsuspecting employees to phishing and malware websites. Be sure to only click links when they’re from a confirmed, expected source, and when they aren’t part of a sales pitch, or an attempt to get information from you.
- Manage A Safe Sender’s List: No matter how new, or costly, or flashy your current spam filter is, it won’t keep unwanted spam out of your inbox forever. Whenever you see that a spammer’s email has made it past your filter, take a moment to block it so that it won’t happen again.
- Do Not Open Unsolicited Email Attachments: This is a crucial email security practice. Suspicious email attachments from unknown or untrustworthy senders are the most common source of malware, ransomware, and other digital threats. Even if it’s from a friend or colleague, consider the message they send along with it; is it worded properly? Does it sound like it’s from them? It’s always a smart move to call the sender or speak in person if possible to confirm that they sent the email. Otherwise, simply delete it until you can be sure of its authenticity.
- Diligently Scan for Viruses and Malware: Another way to double check a suspicious email is to run a malware and virus scan on it. Even though you may have to do so more often than is convenient, it’s always better to be safe than sorry.
Reach out to our team to find out more about the most effective email security practices that can help you keep your business safe. Contact {company} and our IT security professionals at {phone} or {email} today.
From Telegraphs to USENET and How to Protect Yourself from Spam
When someone thinks of spam they typically think of unsolicited bulk commercial email they receive in their inbox. However, the concept of spam started a little earlier than you might think. How far back? How does 1864 sound? Spam in 1864 you say? Yes, in the form of a telegraph, advertising a local dentistry actually. The Telegraph was so much news that the local paper even reprinted the telegraph that was sent to many households, further propagating the message.

More recently, people consider the first spam email coming out of Digital Equipment in 1978 which went to a total of 393 people promoting their latest computer model. You can thank a Monty Python sketch based on a cafe that only served the canned spiced ham SPAM for the origin of the name. Another early spammer was the lawyers Canter and Siegel posting their “Green Card Lottery” message to USENET, a shared messaging system.
What does all this have to do with today? You don’t want to be known as a spammer. There are three ways to attack the spam problem. First off, you don’t want your marketing emails to be classified as spam. Secondly, you don’t want your mail server to be abused where someone sends spam through your hardware. While this wasn’t sent to you directly, your hardware could be blacklisted, thus affecting your own emails. Lastly, you don’t want your employees to respond to spam. There are ways to filter this at the mail server to prevent them from seeing the messages, or at least classify messages as fishy before their opened. Our company {company} can help you to protect your business from being labeled a bad apple in the email business.
Starting with the most important avenue, ensuring your marketing messages get through, there are some best practices to know about. For starters, don’t just send emails directly to your clients. Putting everyone’s email in the “To:” field of a message is bound to cause problems when someone does a reply-all. If you absolutely have to send a message to LOTS of people, it is better to use the BCC (for blind carbon copy) field of a message. Better yet, rely on a mailing list management package like that offered by Constant Contact. Typically, you don’t want to add people to the mailing list yourself. Instead, people should opt-in. More importantly, with each message you send, there should be unsubscribed instructions.
Protecting your mail server is not an easy task. There are some simple steps you can do like requiring that users are authenticated before sending a message, but someone can just spoof the email headers to make it appear messages came through your server. To best protect your server, in 2012 DMARC, or Domain-based Message Authentication, Reporting, and Conformance was introduced. Combined with the earlier introduced SPF, Sender Policy Framework, this makes sure that any messages appearing to come from your mail server actually came from your mail server. {company} can help you keep up with the latest ways to protect your email servers and thus getting your marketing messages through.
Lastly, it is important to look at the inbound side of spam. With all the talk of Russians hacking servers and the release of inappropriate celebrity photos, most of these attempts are triggered by phishing attacks of targets. You still need to worry about viruses being sent through email, but phishing involves fraudsters sending what look like real emails in the attempt to reveal personal information like passwords and bank account info. You don’t want your employees giving away the farm so that others can then get into your company network or your employees worried about identity theft. {company} can help protect your mail servers from letting these unsolicited emails through.
Contact us at {email} or {phone} to learn more about how we can help you.
What Companies Need to Know About Technology Management
Technology Management has become an important aspect of doing business today.
Here are a few details about what it entails, and why a business may need it.

Technology management is a term that is used to refer to a group of services offered to a business that may not have its own IT department. The process can include project management, technology planning, database services, disaster recovery, security, document services, document formatting, e-billing, mailing, mass printing, and much more. Here is some more information I have prepared on this topic. It should help you gain a better understanding of technology management.
Why Do You Need Technolgy Management Services?
The break and fix approach may seem like a good way to save money, but it is going to cost you. Such neglect will eventually lead to a major tech disaster in the future. Such disasters could take the form of tech failure or even a major security breach. Such breaches can lead to class action suits if critical information is lost.
However, having to hire an in-house team may not work either. The inflated costs on the payroll are not worth it for most business owners. When you outsource technology management, the IT infrastructure will receive the care of experts. Best of all, it does not cost an arm and a leg. Additionally, your business will get the full benefit of an experienced team of experts instead of just a few IT experts working in-house. Some of the benefits are:
- Proactive Management.
With technology management, you do not wait for technology to fail before fixing it. A technology management company will review your equipment often and make upgrades as they may be deemed necessary. Such a company will also ensure that you work with only the best antivirus and malware protection.
- Better Network Administration.
A good technology management company does not just hire fresh college graduates. People that work for such companies usually have years of experience under their belts. They know how to tweak each system to fit into a unique business environment. That way, a company is able to maximize its output. The result is that you will be getting more value for the salaries you pay your employees.
- Automated Monitoring.
A good company will have hundreds of system monitors that will allow them to take proactive measures to deal with any problem. That way, a company does not have to deal with an aftermath of a disaster.
- Technology Consultancy.
All companies have technology needs that continue to grow as the company grows. However, it is not always easy to know what you need unless you have an expert as part of your staff. A technology management company will give you the advice that you need to choose the right technology. That way, you will always have an edge over your competition in terms of technology utilization.
- Real Time User Support.
When you hire a technology management firm, it will not be much different to hiring in-house staff in regards to response time. Most of them can have an engineer at your office in minutes when you need a technical expert to solve an issue. Such an expert will give all the options you have and make a recommendation on which you should choose.
Some of the Cloud Service solutions you can expect.
Most business today use cloud services. A technology management can help you with these services if you use the cloud:
- Spam Protection.
A major downside of the cloud is spam. It takes up valuable space in the cloud. A good tech management company will provide you with solutions that prevent unwanted messages from ever reaching the inbox.
- Data Backups.
Data backup is another important service that you will get as part of the cloud-based solutions. By offering cloud-based backups, you will get the peace of mind that you need to run your business. You will no longer have to worry about losing backup tapes or the tapes were stolen.
What Types of Companies Need Technology Management?
All businesses, no matter how big or small, need some IT support to operate efficiently in the modern world. Such support can be useful in helping them to avert major disasters to their business operations.
However, different industries will have differing needs. Thus, not everyone wants the same kind of IT support. There is no one-size-fits-all that can work for all businesses. Some of the businesses that may need Technology management are:
- The Financial Sector.
A good tech management firm will provide you with a clear understanding of the current state of your systems. They will identify the vulnerabilities, risks, and prioritize the issues that are discovered. Additionally, they can also help you identify what has been changed since the last audit took place.
- Manufacturing.
Most people think of the manufacturing sector as the huge processing plants and large warehouses. However, these companies have office buildings that allow them to process the paperwork. If the back office operations are not efficient, an office could lose a lot of money. A technology management firm will help you keep an eye on the IT systems to ensure that they are always working well. That way, a company can focus on its core duty of manufacturing.
- Professional Service Industry.
Downtime is more than just annoying to customers. It can have a huge impact on the profitability of a company. Instead of waiting for equipment to break down, the company will often conduct assessments at regular intervals to prevent downtime. Less downtime will mean that employees have more time to work on their projects. Additionally, it will help to keep your customers happy.
- Non-Profits Operations.
Cyber security must be the priority of every business. There is a lot of malware being created all the time. A breach to a company’s network can have a crippling effect on its finances. The effects can be worse for non-profits since they rely on donors. If donors feel that you are not taking care of their money, they will simply move on. A good technology management company will help to ward off any criminals that may want to reap where they never sowed
WannaCry thoughts for Mac Users.
Its a mess, but we have some advice, some actions to take, and have compiled places you can go for more info.
By now you have seen the news, probably had people ask you if you were hit, and wondering if you needed to be freaking out! (Hint: If you are a Mac user, you are mostly safe at the moment- we’ll explain mostly later)

What is/was WannaCry?
WannaCry was a large cyber-attack affecting more than 250,000 computers in 50 countries. Like past ransomware, the assault started spreads by phishing email messages. Typically, a user will click a link in a bogus email and accidentally download the Malware onto their system. Where WannaCry was more vicious than previous RansomWare attacks is that once it has infected a PC on a network it can spread like a worm to other non-patched computers. It was built by utilizing the Eternal Blue abuse created by the National Security Agency. (Read about some Lessons we can learn from WannaCry from the Washington Post.)
Mac users dodged a real bullet on this one, as the WannaCry RansomWare attack only effected Windows computers, but now is the perfect time to make sure to double check and be sure you are prepared for future attacks as it is clear that RansomWare is here to stay.
A couple really important things to keep in mind.
Be smart. Be thoughtful.
Make sure you, your employees, friends and family are smart as well.
- Beware of phishing attempts. Know the sender of any email you open. Validate the sender. Did you know you can hover over the sender in your mail app to verify the address it came from, if it doesn’t look right, it isn’t.
- Your… Bank, Church, School, Store, Tech Support Guy, Apple… won’t or shouldn’t be asking you for sensitive info in an email.Don’t click the link unless you absolutely 100% know its legit. Go directly to their website to change any info, and never do it from a link in an email. Again you can hover over links in emails to verify the validity of the link. -> Pay attention to the last part of the address before the .com if it isn’t what you expect don’t click!
- Make sure you have the latest security updates installed and up-to-date. (We have a service that can/will do that for you if you are interested)
- Back Up Your Data! Religiously. And to the cloud also. Your data doesn’t exist unless it is in 3 places, period. (We have a service that can/will do that for you if you are interested)
- Running windows on your Mac? Be sure to run your Windows updates. Monthly, without fail.
- Use unique and complicated passwords and use a password manager. Our favorite is 1Password, but others are good too. At a minimum, leverage Apple’s built in Keychain.
Want some more reading?
Take a gander at the volumes of password and security advice from our blog. (CreativeTechs.com)
How a 22 year-old stumbled on the kill switch. But it only slowed it, and the next wave is just starting. (Cnet.com)
Windows users: Heres the links to the Microsoft Patches for effected machines. (Microsoft.com)
Be safe out there and call or email us if you have questions or need help,
The Creativetechs Team
Is Your Smart Data Truly Private?
Find out how to make your smart data truly private – from everyone.
If it wasn’t enough to worry about private hackers tapping into our devices and data, the latest leaks from Wikileaks also show that agencies like the CIA have the capability to hack into everything from phones to TVs. While it’s illegal to spy on American citizens like this, the fact that the technology exists is far from comforting – which is why it’s so important for people and companies to make sure their data remains safe and private. Let’s go over several of the best ways stops even skilled hackers from accessing your information.

Guard Your Email
One of the most common ways agencies like the CIA get access to information (along with many other hackers across the world) is to only ask for it. The old tricks tend to work best, which is why phishing schemes, where hackers pretend to be from friends, family, banks, or other trusted organizations, remain so popular and effective. It’s tough to filter out the best phishing schemes, but fortunately, there’s another classic defense: Pay close attention to what you read! Don’t assume that every email you get is honest, and don’t believe an email just because it “looks” official and includes personal information. Never, ever clink on links in emails that you don’t absolutely trust.
Create a VPN (and Avoid Unsecured Networks)
A VPN or virtual private network is the top suggested solution for people worried about privacy. These systems, available both for free and with fees for more advanced versions, create an encrypted channel to a remote server and pass all internet data through that channel so that your IP address remains hidden. This can be useful when it comes to privacy, but a VPN is only worthwhile if you consistently use it. It’s also important to note that some VPN providers have a better reputation than others when it comes to their security and services.
A slower, more effective browsing option would be to use something like Tor browsing and encryption, which has gained notoriety as the premiere way to access the “Dark Web.” Tor offers more complete encryption of Internet activities, but it also tends to massively slow down your Internet speed and make downloads more difficult.
Encrypt Your Messaging
We send a lot of information via messaging apps these days. Unfortunately, messaging apps aren’t necessarily secure, and if Wikileaks is accurate, there are methods to retrieve chat information from them. The best options here are encrypted messaging tools that work harder to protect all the data in your conversations. This is one reason that WhatsApp has become more popular since it offers high-level encryption compared to many other tools. It’s also worth noting that Android platforms appear to be more vulnerable to chat hacking than other devices. Android, in general, is a more open platform than iOS (and far more open than Blackberry), which means that it can experience vulnerabilities that may not apply to other operating systems.
Encrypt Your Hard Drive
Many programs, including TrueCrypt and BitLocker, allow you to backup and encrypt it. Hard drive encryption is often under-utilized when it comes protecting data, but it does make accessing data much more challenging if a hacker has managed to gain access to your files or operating system.
Be Careful With Any Devices that Watch or Gather Information
As a general rule, if you have a device that can collect environmental information, that means someone else may be able to tap into that information as well. There are two typical examples used these days: The first is IoT or Internet of Things devices, the smart devices around homes and offices that include plenty of sensors picking up data. Because this data is transmitted on wireless networks, it’s far from secure – and often easier to hack than our conventional mobile devices. The other example is computer webcams, which are so easy to hack and control from a distance that today’s computer experts often use cam covers or even pieces of tape to block cams when they aren’t actively used.
Always Turn Devices Fully Off (Especially When Traveling)
This is a major step for all employees and family members that want to keep their devices secure. There are multiple ways to hack into mobile devices if they are turned on, especially with the random networks that you tend to run into when traveling. The absolute best way is to turn devices fully off (no “thumbprint to sign in” screen, fully off).
Guard Your Passwords Well
Do you know the easiest way to hack into protected data? Find the password. Since passwords are often written down nearby or clumsily made, it’s easy for hackers and yes, law enforcement, to break into encrypted data with a few necessary tools. So choose good passwords, and make sure those passwords are protected, preferably by keeping them only in your mind.
For more information about protecting your data in {city} or while traveling, contact {company} at {email} or {phone} to learn more about protection and privacy services!
Wisdom Wednesday: Sifting Through Spam: Understanding The Dangers Of Junk Mail

Every day, businesses and individuals send over 205 billion emails all over the world. Though many of these messages contain valuable information, a significant portion of them are spam. Receiving or sending spam exposes your business to a variety of risks, including:
Ruined Reputations
Many firms are unaware that their email accounts have been compromised, sending spam to current and future clients and partners. This can quickly ruin your company’s reputation and make it harder for you to succeed in the long run. If clients and customers think you’re sending them spam intentionally, they will view you as untrustworthy. Even when they realize your accounts were hacked, they may conclude that you do not understand IT issues or take them seriously. Thus if anyone reports that you have been spamming them, you must promptly apologize and put a stop to the problem.
Malefic Malware
Be wary of spam messages that you receive, as they could harbor viruses, trojans, and other harmful programs. Malware can lock you out of vital programs, provide unauthorized access to sensitive information, or even crash your entire computer system. You should thus never open messages you suspect to be spam. If you don’t realize an email is spam until you have already opened it, do not reply to it or click on its links— not even to unsubscribe from the mailing list. The more you engage with spam, the more opportunities it has to transmit critical programs.
Subtle Scams
In addition to infecting your computer systems, spam writers also use more subtle tactics to cheat you. Junk mail may come in the form of a fake business offer, using the name and writing style of a real company that could be a potential supplier or partner. The scammer will try to convince you to pay them, supposedly for a service or venture that will help your business; if you comply, they will take your payment and leave you with nothing. To separate scams from real business propositions, look up the companies that claim to be sending the emails and contact them independently. If a company has no record of sending the message, the offer is not real.
Data Deliverance
Besides stealing money, scammers can also use spam mail to get you to hand over sensitive information. Phishing scams involve sending you mail under the name of a company or individual you trust, such as your bank, your health insurer, or one of your employees. The message will ask you to send over sensitive information that the company or individual would have access to.
In general, you should never send sensitive information over email, to begin with. If you do receive a message from a trusted entity demanding such information, contact them at a different address or meet with them to confirm their request. Never expose your business to phishing scams.
{company} strives to protect businesses throughout {city} from spam and all other risks. To learn more, call us at {phone} or contact {email} today!
Get A Robust Line Of Defense Before Cyber Attackers Strike!
Common Sense Mac Security Precautions
The security of your business is something that must be taken seriously.
Our cyber security offerings are an extension of our Total Support plan.
Although Mac computers do not typically face the same threats as Windows computers, there is still a need to be vigilant and protect your network.
Protecting what you have worked so hard to achieve is by no means “Mission Impossible.”
We have the training and the tools to give you the right balance of security and flexibility.

Email Security
Many email servers have little to no security built into their programs. By implementing our spam-filtering program, we keep the junk out of your inbox.

Managed Firewall
We keep a close eye on your firewall’s infrastructure to detect any threats that could compromise your network.

Active Monitoring
All computers can experience vulnerabilities – including Macs. We will monitor all computers and mobile devices for anomalies and potential threats.

Human Error Avoidance
The biggest source of security vulnerabilities is employee error. The simple truth is that many people just don’t know safe online practices. We can help.






