Use Your Apple Watch to Unlock Your Mac, and Apps in Catalina
What Does Having a T2 Chip in Your Mac Mean to You?
Some of Our Favorite Features of macOS 10.15 Catalina
Here’s How to See Full URLs in Safari’s Smart Search Field
Here’s How to See Full URLs in Safari’s Smart Search Field
By default, Safari on the Mac hides full Web addresses—technically known as URLs—from you, showing just the site name in the Smart Search field at the top of the window. If you click in the field or press Command-L, the full URL appears, which is good for checking that you’re really where you think you should be and not on some dodgy site. It’s also useful if you need to copy just a portion of the URL to share or otherwise work with. To make that check easier, go to Safari > Preferences > Advanced and next to Smart Search Field, select “Show full website address.” Then you can verify that the URL looks right with a glance.

(Featured image by Matthew T Rader from Pexels)
Tips to help you keep security top of mind…
More great tips from the archives…
- Two Secret Key Combos for Forward Delete on the Magic and MacBook Keyboards
- iCloud Photo Library Users: Do NOT Turn Off iCloud
- Ever Wondered Which Words to Capitalize in a Title? Use Capitalize My Title!
- Tips for Setting Up a Comfortable and Effective Home Work Space
- Tips for Better Videoconferencing
- Set Your Preferred Name and Photo for Messages on iOS
- The Fastest Way to Change Wi-Fi Networks in iOS
- What to Put at the End of Your Emails
- Apple Business Manager Is a Win for Apple-Driven Workplaces
- Find Wasted Space with Storage Management
- Forrester Research and IBM Studies Show Macs Are Cheaper than PCs
- Being an Apple User Means You’re Not the Product
- How to Ask for Tech Support So You Get Good Answers Quickly
- Apple Business Manager Is a Win for Apple-Driven Workplaces
- The Hidden Dangers of Shadow IT on your business
- Need to Stay in Touch? Try One of These Videoconferencing Apps
- Never Send Someone a Password in Mail or Messages: Do This Instead!
- What Are All These New Privacy Request Dialogs in Mojave?
- The Importance of Productivity Tech for Your Road Warriors
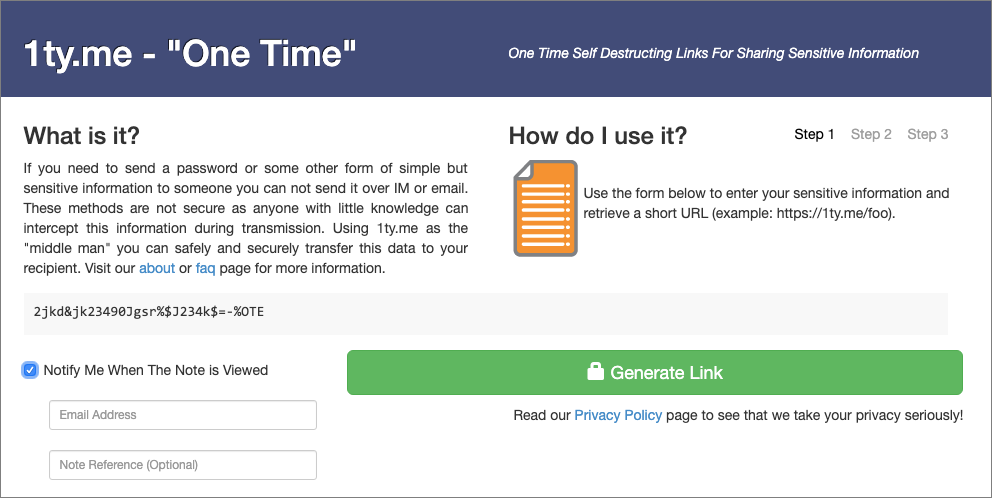
Never Send Someone a Password in Mail or Messages: Do This Instead!
One of the big no-nos with passwords is sending them to other people as plain text in email or a text message conversation. You presumably trust your recipient with the password, but what if their email was hacked or phone stolen? Instead, always use a site like 1ty.me or One-Time Secret, which lets you turn a password into a Web link that can be opened only once. (Not sure about those sites, we have built our very own password sharing site, secret.creativetechs.com that you can use.) Send that link to the recipient, and when they get the password out, they can store it in a secure password manager like 1Password or LastPass.
(Featured image by Kristina Flour on Unsplash)
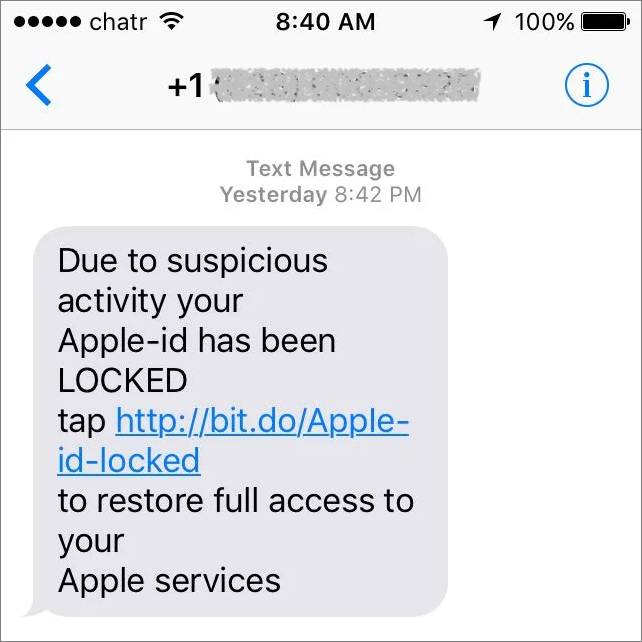
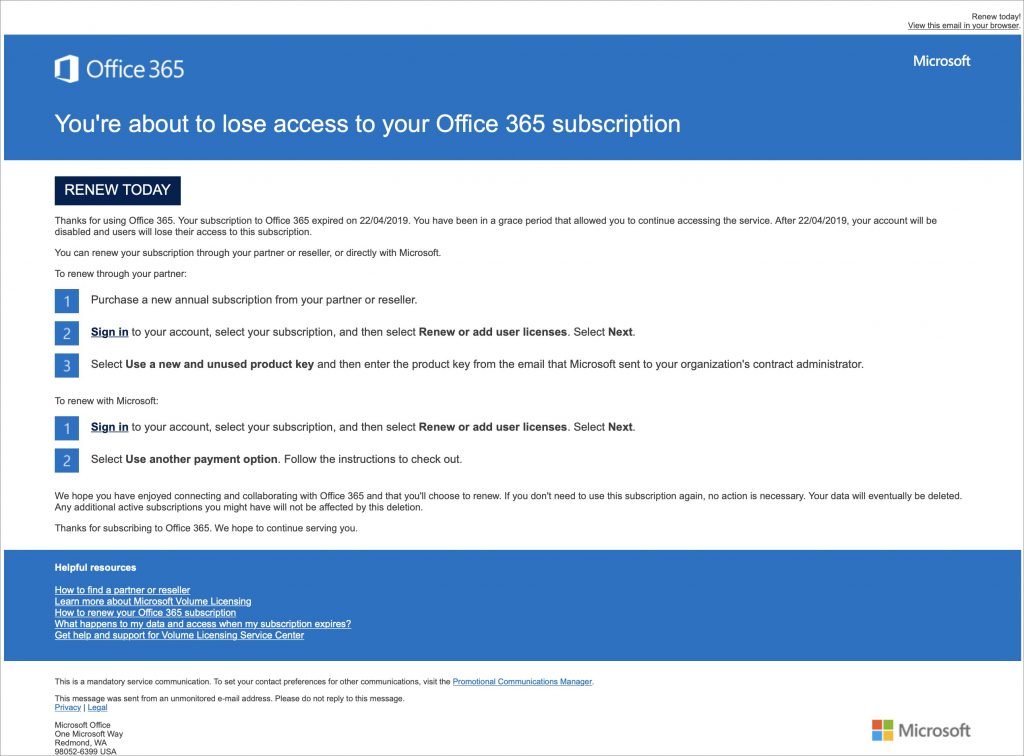
Beware Microsoft Office 365 Phishing Attacks!
We’re seeing an uptick in email phishing attacks purporting to come from Microsoft about Office 365. They’re quite convincing messages that tell users that their credit card payment has failed, that an account needs renewing, or that a password needs to be confirmed. Needless to say, they’re all complete scams, and clicking a link in them takes you to a malicious Web page that will try to steal your password or credit card details. As we noted in “Gone Phishing: Five Signs That Identify Scam Email Messages,” large companies never send email asking you to click a link in order to log in to your account, update your credit card information, or the like. Hover over links to see where they go before clicking anything, and stay safe out there!
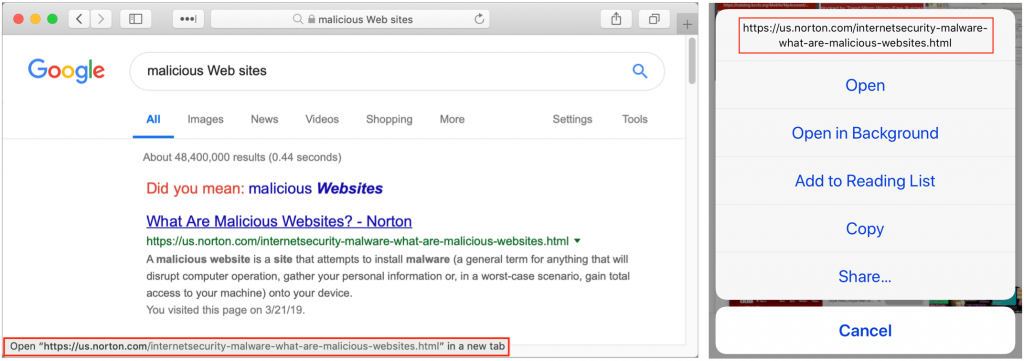
Look before You Leap with Safari’s Link Preview
When you follow a link in Safari, you generally don’t know where you’re going to end up. That’s fine most of the time, but what if you’re concerned that a site might be trying to trick you into going somewhere malicious? Safari provides an easy way to look at the URL under a link. On the Mac, choose View > Show Status Bar, hover your pointer over the link, and look at the bottom of the window. In iOS, touch and hold a link (don’t press for 3D Touch) until a popover appears, showing the link and giving you options for opening it. The most important thing to look at is the domain—us.norton.com in the screenshots. It should match where you think you’re going, or at least look reasonable. If the URL is dubious, don’t follow the link.
Block Telemarketing Calls Automatically on Your iPhone
Junk calls are one of the great annoyances of the modern world. You’re minding your own business when your iPhone vibrates in your pocket. You pull it out, curious as to who’s calling, but don’t recognize the number. You may notice that it’s in the same exchange as your phone number, suggesting that it’s a neighbor. But no. When you answer, it’s “Heather,” a pre-recorded voice wanting to sign you up for a resort vacation, give your business a loan, or help with your credit card debt. Angered by the intrusion, you tap the red hangup button, wishing you had an old-style telephone receiver to slam down.
There’s no way to retaliate against these scum-sucking bottom feeders, and the best option is to hang up immediately. For quite a few versions of iOS, you’ve been able to block a caller manually—just tap the i button next to the call in the Recents screen in the Phone app, scroll to the bottom, and tap Block This Caller. But that’s seldom worth doing since telemarketers often spoof the numbers they call from, so it’s unlikely you’d get a second call from the same number.
Instead, we recommend taking advantage of a feature Apple introduced in iOS 10 that enables apps to block calls for you. Quite a few of these apps have appeared, with some of the best reviewed being Hiya, Mr. Number, RoboKiller, and Truecaller. Hiya and Mr. Number are both free and from the same company—Mr. Number is a stripped-down version of Hiya—whereas RoboKiller and Truecaller require an in-app purchase for a monthly membership.
In general, these apps work by receiving caller ID information from iOS and comparing it against both your local contacts (to identify good calls) and a constantly updated database of numbers used by telemarketers (bad calls). Calls from your contacts ring through normally, as do calls from phone numbers not in either of those sets. That’s key, since your doctor might call back from a secondary number, or your kid’s new teacher might call to talk about an upcoming snack day. But if you receive a call from a number known to be used by a telemarketer, the app can either identify it on the incoming call screen or block it automatically, sending it to voicemail.
To enable one of these apps, after you download it from the App Store, go to Settings > Phone > Call Blocking & Identification and enable its switch. You’ll probably also have to do some setup in the app itself, providing your phone number, perhaps creating an account, and determining what should happen with different calls (Mr. Number is shown below, right).

With Hiya and Mr. Number, you can copy a number from the Phone app’s Recents screen (tap the i button for a call, and then press the number to access a Copy button) and then look it up to learn more and see comments other users have made. And if you get a telemarketing call from a number that the app doesn’t recognize, you can submit it to protect others.

RoboKiller claims that it wastes the telemarketers’ time by playing pre-recorded “Answer Bots” conversations to keep them on the line, preventing them from calling more people.
Details vary by app, but the only real downside to using one of these apps is that it may ask for information about you or your contacts to improve its services. If that feels intrusive, investigate one of the apps that requires a membership, like RoboKiller, to see if it better answers your concerns.
In the end, it comes down to how many telemarketing calls you receive each day, week, or month. If you’re lucky and get only one or two per month, it’s probably not worth messing with a call blocking app—maybe just send unidentified (and unexpected) calls to voicemail. But if you’re interrupted by multiple junk calls per day or week, give one of these apps a try and let it reduce the onslaught.
Gone Phishing: Five Signs That Identify Scam Email Messages
Ignore Unsolicited Calls and Texts from Apple and Other Tech Companies
We don’t want to belabor the point, but multinational tech companies like Apple, Facebook, and Google will never call or text you personally out of the blue. So if you get a call or text purporting to be from such a company, it’s 99.9% likely to be a scam, and you should ignore it regardless of whether the caller ID seems legitimate. If you’re still worried, look up the company’s tech support phone number separately—never respond directly to such a call or tap a link in a text—and discuss the situation with the support reps. Or contact us, and we’ll talk it through with you.